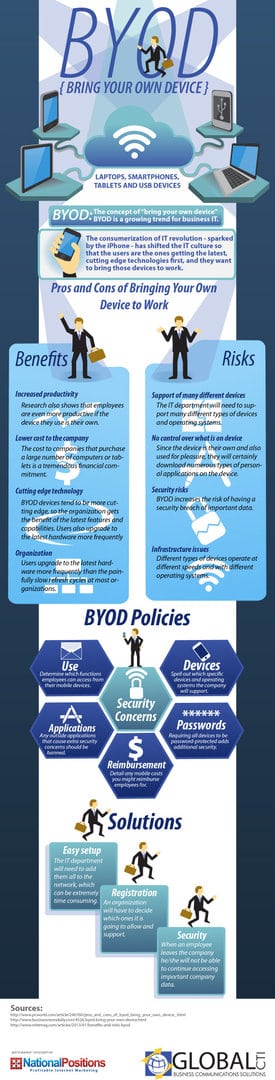
BYOD is a growing trend in the workplace for “bringing your own device,” the concept of which involves bringing your personal laptops, smartphones, tablets, and USB devices to work as opposed to using company-issued devices. This newer concept faces some criticism, as it poses great benefits, as well as a few risks. What is key here is having companies who implement this policy consider the risks involved and come up with solutions to combat those problems.
Research has shown that bringing your own device to work has not only brought increased productivity among employees and lowered costs to the company, but it has also provided organizations with cutting edge technology, as BYOD devices tend to be upgraded more frequently and include the latest features and capabilities. However, not all good things come without posing risks. Since employees will be bringing in all their own unique devices, the IT department will not only need to manage supporting the various operating systems and speeds, but they will also have to work at preventing security breaches as well. Therefore, it is important for companies to implement tailor-made policies and solutions when using BYOD.
These solutions for BYOD management will include:
- An easy setup where all employees will have access to the same network
- Registration for allowing and supporting certain devices
- Security forum where employees will no longer have access to company data after leaving the company
BYOD is quickly on its way to revolutionizing not only the workplace but other systems where laptops, smartphones, and tablet devices are frequently used. Before your company decides on implementing this policy, it is vital they familiarize themselves with the possible risks involved. Once guidelines for BYOD solutions are implemented to avoid these risks and security concerns, it will prove to be a fluid and essential aspect of workplace productivity.