Today’s topic address environments where CAT3 voice cabling can be utilized to support Power over Ethernet (PoE)
Overview
Sometimes you may run into an environment where you need to place IP phones but do not have the data cabling infrastructure to support it.
There is a product that allows for CAT3 cabling to support PoE, made by a company called Phybridge.
Phybridge is a ShoreTel Technology Partner
Phybridge – UniPhyer and PhyAdapter http://www.phybridge.com/
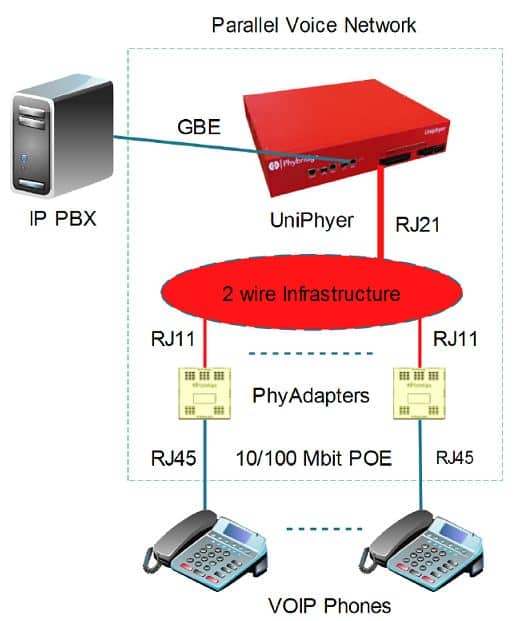
The product UniPhyer, allows for PoE and Ethernet over a single pair of wires.
UniPhyer comes in two models:
- LB-UA2324 – A 24 port support 24 or 26 gauge single twisted pair wire
- LB-UA2348 – A 48 port support 24 or 26 gauge single twisted pair wire
At the telephone end, a PhyAdapter is used to provide the interface from the single pair wire (RJ11) to the IP phone (RJ45). It does this via ADSL2+ technology.
The UniPhyer provides a permanent point-to-point link between the IP Phone jack on the PhyAdapter and Phybridge UniPhyer and is thus able to guarantee predictable communication between the two end points.
IP Telephony deployed on a Phybridge platform benefits from this topology and does not require elaborate buffer mechanisms to handle out-of-sequence packets and delays due to the multiple hops and multiple paths that packets take in a traditional LAN.
IP Telephony systems deployed over the Uni-Phyer can thus offer the robustness of traditional telephony systems and the easy mobility of IP devices. The LAN independence of the UniPhyer platform makes IP telephone systems better able to handle network outages. The UniPhyer provides a singular power source eliminating the need for distributed UPS wiring.