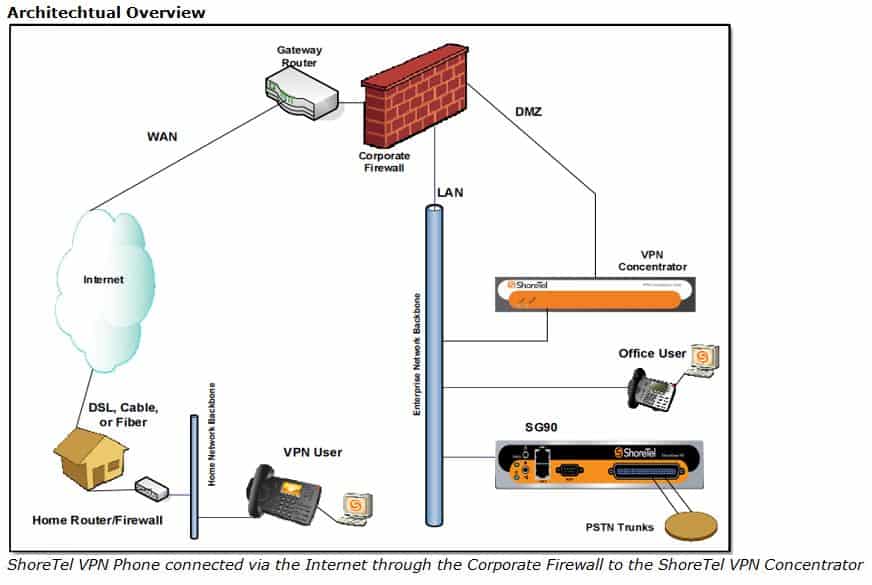
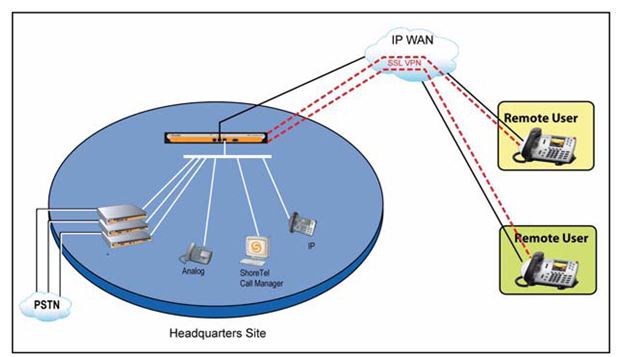
ShoreTel VPN Concentrator and its associated VPN phones
The ShoreTel VPN Concentrator and VPN IP phones was introduced to the ShoreTel product line in software release 8.1
The VPN Phone is a ShoreTel feature that provides secure audio communications for ShorePhones located remotely from ShoreGear switches through open VPN SSL tunnels.
Use of a ShoreTel VPN phone permits a person working in a SOHO environment to take advantage of a physical phone at their remote office location. The phone is truly an extension on the corporate ShoreTel system and grants all of the capabilities of the system to the remote user including features like transfer, conference, directory and UC functions such as voicemail and presence. Once properly setup, the VPN phone becomes an integral part of the home office environment. Having a good VPN system is important in working from home to ensure that documents and client information is shared efficiently and privately. There are many VPN services out there, so by reading reviews such as the NordVPN Review, you can get a better idea of what is available to help your business.
Background:
Prior to the release of the VPN phones, ShoreTel utilized two methods of support IP telephony from remote SOHO locations.
- Office Anywhere provides toll quality voice, easy setup and Call Manager access at the expense of incremental toll charges and the loss of IP telephony features.
- SoftPhone provides easy deployment, no incremental toll charges, and Call Manager access at the expense of unpredictable voice quality, PC dependence, and the loss of IP telephony features.
With the addition of the VPN Concentrator and VPN phone, it added an additional remote IP telephony method.
- Remote VPN IP phone provides access without incremental toll charges, Call Manager access, and IP telephony features at the expense of unpredictable voice quality and a complex deployment.
To support the VPN phone, Version 8.1 also introduces two VPN Concentrators capable of supporting up to 100 calls through VPN tunnels.
The ShoreTel IP phones that support the VPN Phone feature today are:
- IP-230g
- IP-560g
- IP-565g
- IP-655
The two VPN Concentrator models available are:
- VPN Concentrator 4500 – Capable of supporting up to a maximum of 10 concurrent VPN phone connections
VPN Concentrator 5300 – Capable of supporting up to a maximum of 100 concurrent VPN phone connections
Feature Summary
VPN Phone provides secure audio communications for VPN ShorePhones located remotely from ShoreGear switches through open VPN SSL tunnels.
The feature includes an Open SSL VPN client in the ShoreTel IP phone and an Open SSL VPN Gateway.
The Open SSL structure allows the traversal of firewalls implemented by many enterprises for blocking VPN tunnels.
Components
VPN Phone implementation requires two components – a VPN Concentrator and a VPN Phone capable of communicating over a VPN Concentrator
The SSL based VPN Concentrator enables remote VPN Phones to establish secure voice communications with through the local ShoreTel PBX through SSL VPN tunnels. For every tunnel, a virtual PPP interface is created on VPN Concentrator and a peer PPP interface is created on the remote VPN Phone.
Signaling and media streams go through the PPP interface and are secured by SSL encryption.
Licensing is also required for the number of concurrent VPN phone connections. This licensing is assigned to the VPN Concenrator.
Each VPN phone also requires the standard extension and mailbox license as with any normal IP phone would.
Terms
- Secure Socket Layer (SSL): a cryptographic protocol that provide secure communications on the Internet.
- Point to Point Protocol (PPP): a data link protocol used to establish a direct connection between two nodes over serial cable, phone line, trunk line, cellular telephone, specialized radio links, or fiber optic links
- Virtual Private Network (VPN): a computer network in which some internode links are facilitated via open connections or virtual circuits through a larger network instead of via physical wires. The link-layer protocols of the virtual network are said to be tunneled through the larger network. One common application is secure communications through the public Internet.
- VPN Concentrator: a gateway that provides secure access to a corporate network for remote devices through VPN tunnels.
- Stunnel: a multi-platform program that provide SSL tunnels between a remote device and a VPN gateway.
- Tunnel: an link between two networks (such as LANs) that are connected by a larger network (such as a WAN or the Internet). Tunnel packets containing messages exchanged by the smaller networks are encapsulated into packets that facilitate routing through the larger network. Each VPN communication session establishes a tunnel, which is removed when the session is finished.
Stunnel Establishment – ShoreTel VPN Phone Implementation Architecture
Each remote device is assigned a username and password that is recognized by the VPN Concentrator.
Phone logging into the Concentrator are authenticated through the verification of its username and password. When the phone is successfully authenticated, the Concentrator establishes a stunnel to that phone, after which it can receive and make phone calls through the ShoreTel system.
The stunnel remains in place until the phone sets the VPN parameter to off or the Concentrator times out all stunnel connections.
Establishing a stunnel requires an available VPN phone license.
If the number of active stunnels equals the number of available licenses, The VPN Concentrator will not establish new stunnels until an existing stunnel is disconnected. If you’re interested in finding a great VPN service, check out vpn service reviews.