Endpoint protection involves all the practices, protocols, tools, and teams involved in upholding your business’s endpoint security. An endpoint refers to any device that connects to your corporate network, such as a computer, smartphone, or IoT device.
Endpoint devices can easily become entry points for cybersecurity threats. For example, if an employee’s smartphone is infected by a virus on a public Wi-Fi network, that virus can spread to other devices in your business network once that employee connects the infected phone to your office Wi-Fi.
| “Even a small business network has a lot of connected endpoints. You can’t possibly track them all without the help of an endpoint security solution.” – David Kaiser, CEO/President, Global CTI |
The purpose of endpoint security is to prevent situations like that. It may involve consistent network monitoring or an automated endpoint detection and response (EDR) tool that scans all connected devices for possible threats.
If you’re considering endpoint security solutions, let this article be your introductory guide to what your options are and what you should consider.
How Does Endpoint Protection Work?
Endpoint protection works through software that is installed on network-connected devices. This software actively scans and monitors data flowing through the device. If any malware or suspicious activity is present, the software will identify the issue, log it, and may automatically respond to it.
What is The Difference Between Endpoint Protection and Antivirus?
Although similar, endpoint protection software is not quite the same as antivirus. The main difference is that endpoint protection tools defend against all forms of cybersecurity issues while antivirus tools only protect against viruses and malware.
For example, endpoint protection tools can identify and stop a hacker trying to access your device, antivirus software wouldn’t even notice the attempt if it’s not malware.
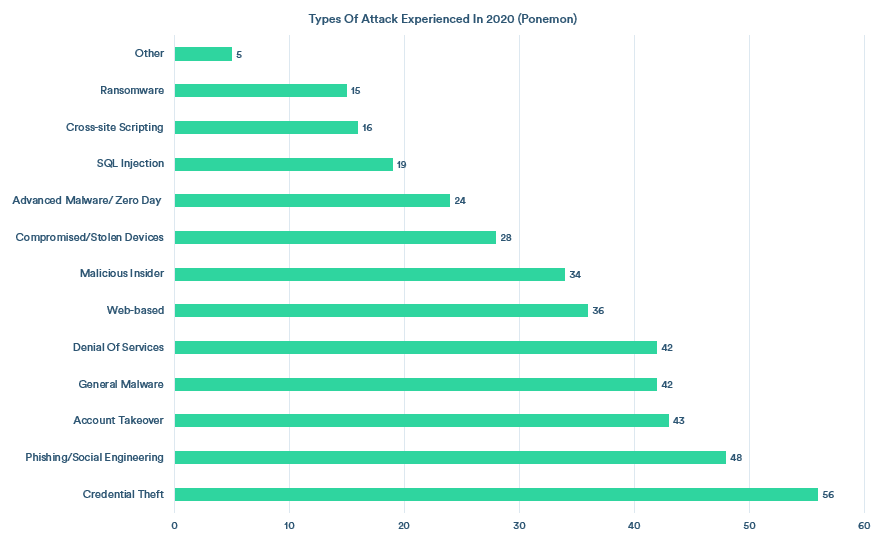
Most prevalent endpoint attacks according to Ponemon; ExpertInsights
What Are Your Endpoint Protection Options?
Endpoint protection isn’t a single tool. You have several options if you want to bring endpoint security to your SMB. Here are a few options.
Endpoint Detection & Response (EDR)
Endpoint detection and response (EDR) is a security tool that watches over your computer systems to spot and handle cyber threats. It keeps track of activities on your network and helps to spot unusual or harmful actions quickly. When it finds something unusual, like a suspicious download, it takes action to handle the issue and also sends an alert to your IT team.
An EDR solution actively watches all activities to find new, unknown threats by recognizing suspicious patterns. This means it can spot and stop new types of attacks that other security tools might miss. It also logs detailed information about these threats. This helps IT professionals understand how attackers work so they can improve security over time.
Endpoint Protection Platform (EPP)
An endpoint protection platform (EPP) consolidates numerous security tools into one unified solution. It integrates antivirus capabilities, firewalls, and other protective features to guard against a myriad of potential attacks.
An EPP makes it easier for you to track all of your cybersecurity tools because everything is centrally managed. Additionally, because it offers a range of tools to protect against many different kinds of threats, you can keep your digital devices safe from various angles
Next-Generation Antivirus (NGAV)
While antivirus tools aren’t typically part of endpoint protection, next-generation antivirus (NGAV) is an exception. That’s because it’s totally different from typical antivirus software tools because it uses artificial intelligence and machine learning to identify harmful activities or files, even if they’ve never been seen before.
By comparison, most antivirus software tools compare data to a database of known threats. NGAV enhances this protection by bringing in a more advanced, predictive capability.
Network Access Control (NAC)
Network access control (NAC) is a network security technology that manages who or what can connect to a network. It sets rules and policies that control access to the network, ensuring that only authorized users and devices can connect to and interact with it.
This tool minimizes the risk of unauthorized users or compromised devices introducing threats into the environment. It also allows organizations to have better control over their network.
Secure Email Gateway (SEC)
A secure email gateway (SEG) is a security solution that protects your email traffic from threats like phishing attacks, malware, and spam. It scans all incoming and outgoing emails, filtering out harmful content and blocking threats before they reach your inbox.
Email attacks are the most common way that successful data breaches occur. So, robust email protection is vital. By filtering emails for harmful content and blocking potential threats, SEG ensures that your communications remain confidential and secure.
What to Look For in an Endpoint Security Provider For Your Organization
Many different vendors provide many different security technologies. You should look for someone who understands your business vertical and possibly can provide more than just endpoint protection. This is a great way to ensure you get more from your investment.
Regarding the endpoint security solution specifically, here is what you should look for.
Quick Detection & Reaction Time
When it comes to cybersecurity, time is of the essence. Once a threat is detected, the speed at which your endpoint security provider can detect and respond to it is crucial. Opt for a provider that showcases swift detection and reaction times. This ensures that any potential threats are mitigated before they can inflict significant damage.
Human Involvement
Most endpoint security tools work automatically. This is convenient, but it does run the risk of false positives. Algorithms don’t know what’s happening at your business the way that humans do. What it views as suspicious may be an expected unusual activity. For instance, a new log-in from a remote location.
This doesn’t mean that automatic tools are bad. It means that finding the right balance between automation and human involvement will prevent false positives. Look for a provider with a hands-on security team that complements their great system.
Cloud-Based Capabilities
While the cloud is generally more secure, 45% of security breaches begin in the cloud. This isn’t because clouds are less secure, but because many cybersecurity measures only work for onsite data. For this reason, it’s important to ensure that your endpoint protection provider supports cloud security.
| How Else Can You Ensure Secure Connections? |
24/7 Monitoring & Recording
Cyber threats do not operate on a 9-5 schedule, and neither should your endpoint security provider. Choose a provider that offers 24/7 monitoring and recording of all activities across your network. This ensures that any unusual activities or potential threats can be detected and dealt with promptly, even outside of regular business hours.
Integration With Other Software Tools
Your endpoint security solution should be able to work cohesively with other security and management tools in your organization. This not only enhances the overall security posture of your organization, but also ensures that your IT team can manage your security efficiently.
Look for a provider that offers API integrations and compatibility with other commonly used tools in your industry.
Trust Your Endpoint Protection With Someone Who Gets SMBs
You have a lot of options when it comes to endpoint security. However, many endpoint security providers are geared towards enterprise networks. While this shows experience and the ability to manage a high number of endpoints, these providers may or may not truly understand the unique needs of SMBs.
Global CTI can offer enterprise-grade endpoint protection with an SMB mindset. We’re an SMB too, so we get that your business may not have the same concerns as a large enterprise. Still, we’re highly adept at handling the evolving threat landscape and are more than happy to scale our service with your growing business.
With our D.U.N.E (Data, User, Network, and Endpoint) approach, we ensure a 365-degree, robust, and thoughtful cybersecurity strategy that safeguards every facet of your business.
Contact us today to learn more about how we can help secure your sensitive data.


