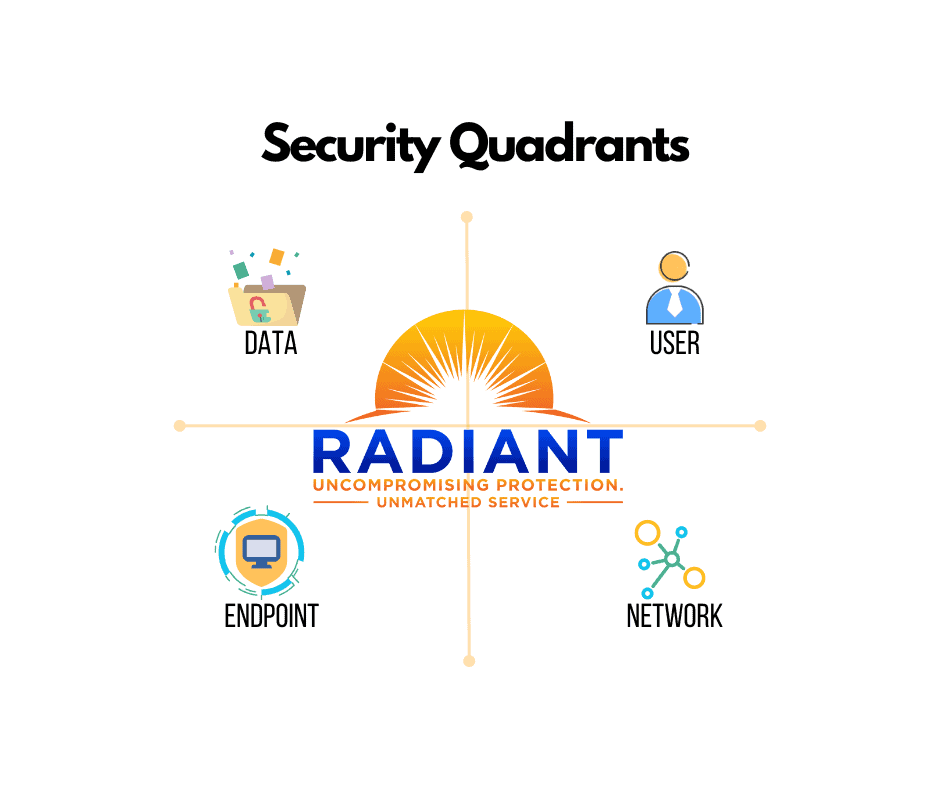
Cybersecurity is a necessity in today’s business world. How can you be sure your organization is fully protected from outside and inside security risks such as ransomware, malware, and data hacks? With so much on the line, it can seem like adversaries have all the advantages. Global CTI can help you take the power back.
We are a united team of defenders using AI-Driven security to predict, understand, and end malicious operations. End attacks in minutes using a unified security approach that enables Global CTI defenders to correlate threat activity across the entire network to protect every endpoint, fixed or mobile.